In February, my colleagues and I hosted an ATM security webinar primarily focused on ongoing attacks in the U.S., and how financial institutions can protect themselves from them.
In October 2023, the U.S. saw a record number of cyber attacks on ATMs. Most of these were either jackpotting or host spoofing attacks. In this blog, we will be focusing on the latter.
What is host spoofing? The term refers to two variants of attacks. Both illegitimately alter or replace the response that the host sends when an ATM requests the OK for a dispense transaction. In most cases, this is achieved through access to the network cable, but there have also been cases where malware was used to alter the communication between ATM and host. Usually, the normal ATM operation is not impacted by this type of attack.
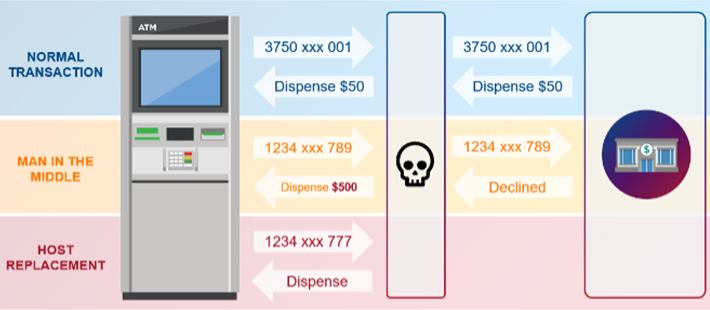
How can you protect yourself from such an attack? Countermeasures that have proven effective over the last years are transport layer security (TLS) and certificate authority (CA) validation. In a nutshell, TLS implements a secure and encrypted network connection between the ATM terminal application and the transaction processor. By itself, this already improves security by a great margin, but there have been cases of advanced host spoofing attacks.
In these cases, ATMs that were not bound to a specific certificate authority were successfully attacked. So, it’s essential to have this second layer of defense. Certificate authority validation ensures that the ATM is not tricked by a fake certificate.
This is just one example of an attack, there are other attacks and risks your ATMs will need to be protected from – cyber or otherwise. For a comprehensive view of ATM security strategy, we have created the 7 shields framework, which provides risks from various directions and strategies to counter them. If you’d like to learn more, get the whole story in our Security Guide: Make your ATM Network More Secure - 7 shields to protect the self-service channel. A great way to start is a security assessment. With Diebold Nixdorf, you have a trusted partner and team of experts at your side. So, consider booking a complimentary assessment with one of our experts.

This blog was focused on host spoofing, but if you’d like to learn more about jackpotting as well, I suggest you keep on reading here.