Protect your users at the ATM from skimming, shimming and other data attacks
In my last blog I talked about the dangers of physical attacks. If you have not read it yet, you can find it
here. While this kind of attack—especially the explosive and hook & chain attacks we talked about—draw a lot of attention due to the extent of visible damage they can do, other attack scenarios are more insidious and no less dangerous.
This time let’s take a closer look at
data attacks. This term refers to all fraud and security incidents aimed at either gaining physical or digital access to card data—in some cases, both. Consequently, the most immediate damage they do is to the consumers whose cards and data, and by extension also their money, are targeted. Of course, consumers who report the fraudulent transaction will likely be reimbursed by their financial institution (FI), but some don’t detect it. While financial losses for banks may not be an immediate issue here, the risk is still large as the damage to the brand can be significant. In a recent study conducted by Nielsen IQ together with Diebold Nixdorf, 90% of consumers who had experienced or even just become aware of a security breach took action: Leaving their financial service provider or reducing their engagement were the most common reactions, but nearly as many shared the experience online or with their friends and family
1. Both scenarios pose a threat to an FI’s business and brand.
By far
the most common type of data attack in the ATM channel is skimming.
First, one should keep in mind that the ATM is not the only point where skimming may occur. It can happen at any point of sale and recently a far more common point of attack is at the gas pump. According to data collected by a U.S. organization comprised of federal, state and local law enforcement and private industry specialists, by far the largest number of skimming attacks—nearly 600 in Q4, 2021—took place at gas pumps. ATMs were targeted far less often with just under 30 reported incidents.
During a skimming attack a foreign device is installed on an ATM to capture data from the magnetic stripe of a customer card. While the location of the device can vary, the defining characteristic of a skimming device is the presence of at least one magnetic read head—meaning that as long as bank cards still have a magnetic stripe, they remain vulnerable. The options for would-be criminals are varied: Overlay skimming, Throat Inlay Skimming, or Deep Insert Skimming devices exist for both motorized and dip card readers and can be bought on the darknet—no expertise required. Today these devices are also much smaller than they used to be, making it harder for unsuspecting users to spot them.
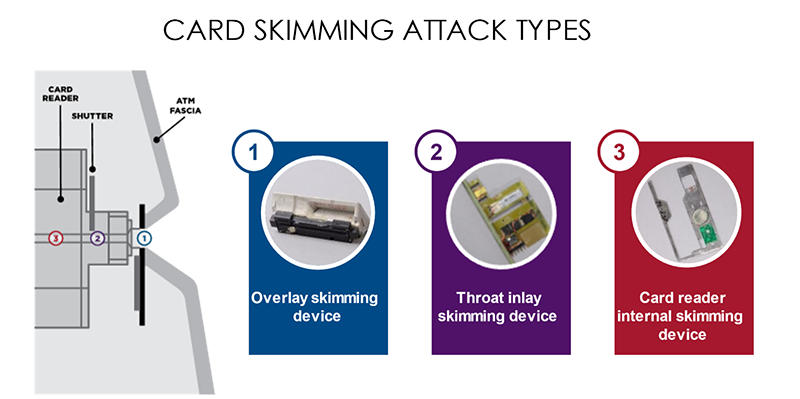
EMV chip technology is an alternative and its use is spreading. In regions where this technology is already widely used, the number of reported skimming incidents has fortunately gone down. But there are regions where usage is still comparably low—and one of those regions is the United States. Unsurprisingly, the risk of skimming attacks remains high when an alternative is missing.
There are also other types of data attacks like shimming and eavesdropping. In all cases attackers attempt to gain data from the card. Like skimming attacks, the most common way of trying to access this data is to tamper with the card reader: collecting data from the magnetic stripe, the EMV chip, or intercepting data that is transferred from the card reader to the PC. While the number of incidents has declined over the course of the last few years, the losses incurred by this kind of attack are still considerable—especially if we take into account the aforementioned impact on an FI’s reputation.
The good news is there are effective methods to prevent skimming and other data attacks. So, what can be done to protect consumers’ data? As the card reader is the primary target for data attacks, it is also the first line of defense:
- Encrypting the communication between the card reader and PC (and other components within the ATM for that matter) protects against eavesdropping on the USB communications and device substitution attacks, also known as Trusted Device Communication (TDC).
- With Internal Space Defense, the design of the card reader is essential to prevent the installation of skimmers and shimmers: by leaving limited physical space within the encrypted read head you can deter the installation of an additional read head.
- A physical barrier—also known as anti-tapping defense—in areas where sensitive information could be exposed can prevent eavesdropping attacks.
- Internal or external Skimming Recognition uses sensors to recognize both internal and external skimmers and set off an alarm or take the ATM out of operation until the issue can be fixed.
- Intelligent Anti-Phishing defense protects against trapping attacks by holding a trapped card with increased removal force inside the card reader—it can later be released with a software command.
- Jamming technology, used in multi-signal jamming and anti-tapping scrambling, protects against external skimming including more advanced stereo skimming attacks and certain types of eavesdropping.
At Diebold Nixdorf, security is always top of mind—it’s part of our DNA as we like to say. That’s why we offer not just the industry’s most secure basic card reader, but also additional Security Packages 1, 2 and 3 which are equipped with even more sophisticated protective measures utilizing the technologies mentioned above—Security Package 3 being the premium solution for deployments in higher risk areas.
Our most secure card reader, however, is
ActivEdge®. Instead of the usual short-edge insertion, this card reader turns data security on its head—both figuratively and literally: The card is inserted long edge first. Then the magnetic stripe is read from side to side instead of front to back, making it extremely complicated for skimmers to capture the card’s information. It has been on the market for several years now and yet remains unskimmed; it’s the best option to protect yourself and your customers from skimmers where EMV chips are not yet offered as an alternative. If you want to find out more about ActivEdge
read this blog by my colleague Marcelo Castro.
By the way: Contactless card readers are (unfortunately) also not impervious to attacks. Keeping your software updated is essential to prevent criminals from getting through the holes in the programming they run on. We’ll explore that topic in my next blog, focusing on cyber-attacks.
In the meantime, if you want to find out which Anti-Skimming solution is right for your needs,
visit us and talk to our experts.
1Nielsen IQ International Retail Banking Consumer and Technology Survey commissioned by Diebold NIxdorf.
